RouterOS 基于VLAN Filtering无线VLAN透传配置
RouterOS支持基于无线链路的VLAN透传。 例如,当我们在一个办公网络中,需要使用一台RouterOS设备分隔办公WiFi和来访WiFi时,可以使用VLAN方式做二层隔离,使用Wlan1做来访WiFi,在Wlan1上创建虚拟AP(VirtualAP Wlan2)作为办公WiFi。 在之前的版本中有相应的解决方案,但v6.41后在bridge增加了VLAN Filtering功能,通过vlan filtering能更好实现无线中vlan透传,也是官方推荐方法。
基于vlan-filtering和wireless vlan-mode (推荐方案)
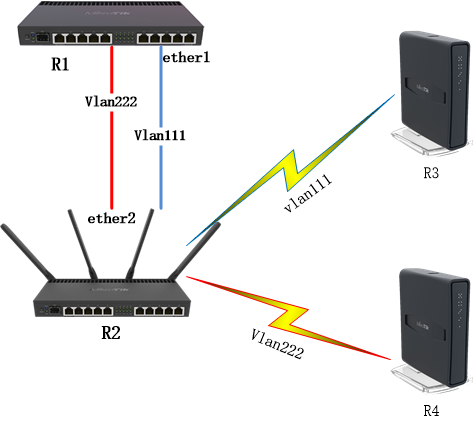
从RouterOS v6.41开始,Birdge增加了VLAN Filtering功能支持二层VLAN转发和VLAN标记处理,因此在v6.41后建议使用以下配置方案。
R1路由器:
在路由器R1创建指定的VLAN接口在对应的ether1有线接口上,即trunk模式的配置,并配置IP地址到VLAN接口,启用三层VLAN。
[admin@R1] >
/interface vlan
add interface=ether1 name=vlan111 vlan-id=111
add interface=ether1 name=vlan222 vlan-id=222
/ip address
add address=192.168.1.1/24 interface=vlan111
add address=192.168.2.1/24 interface=vlan222
R2路由器:
我们需要创建wlan2虚拟机AP接口,并配置Wlan1和Wlan2的加密规则
[admin@R2] >
/interface wireless security-profiles
add authentication-types=wpa-psk,wpa2-psk eap-methods=”” management-protection=allowed mode=dynamic-keys name=\
vlan111 supplicant-identity=”” wpa-pre-shared-key=yusvlan111 wpa2-pre-shared-key=yusvlan111
add authentication-types=wpa-psk,wpa2-psk eap-methods=”” management-protection=allowed mode=dynamic-keys name=\
vlan222 supplicant-identity=”” wpa-pre-shared-key=yusvlan222 wpa2-pre-shared-key=yusvlan222
在路由器R2的Wlan1创建一个虚拟AP接口取名Wlan2,并设置Wlan1和Wlan2不同的无线加密规则,设置vlan-mode=use-tag
/interface wireless
set [ find default-name=wlan1 ] disabled=no mode=ap-bridge security-profile=vlan111 ssid=vlan111 vlan-id=111 vlan-mode=use-tag
add disabled=no master-interface=wlan1 name=wlan2 security-profile=vlan222 ssid=vlan222 vlan-id=222 vlan-mode=use-tag
路由器R2创建桥接,设置vlan-filtering=yes,添加相应的桥接端口,并在bridge vlan中创建对应端口的vlan id标签
[admin@R2] >
/interface bridge
add fast-forward=no name=bridge1 vlan-filtering=yes
/interface bridge port
add bridge=bridge1 interface=ether2
add bridge=bridge1 interface=wlan1
add bridge=bridge1 interface=wlan2
/interface bridge vlan
add bridge=bridge1 tagged=ether2,wlan1 vlan-ids=111
add bridge=bridge1 tagged=ether2,wlan2 vlan-ids=222
提示: 一些RB和CRS设备集成了交换芯片,能实现以太网二层数据交由交换芯片做线速转发,启用桥接VLAN filtering功能后无法实现交换芯片线速转发(除CRS3xx系列设备),则会交又CPU处理。由于无线接口没有归属于交换芯片,因此也无法实现硬件转发,只能交给CPU处理
R3路由器:
路由器R3,添加对应VLAN111的IP地址到Wlan1接口,并创建与VLAN111相同的加密配置,设置无线网卡wlan1的mode=station
[admin@R3] >
/interface wireless security-profiles
add authentication-types=wpa-psk,wpa2-psk eap-methods=”” management-protection=allowed mode=dynamic-keys name=\
vlan111 supplicant-identity=”” wpa-pre-shared-key=yusvlan111 wpa2-pre-shared-key=yusvlan111
[admin@R3] >
/ip address
add address=192.168.1.3/24 interface=wlan1
/interface wireless
set [ find default-name=wlan1 ] disabled=no mode=station security-profile=vlan111
R4路由器:
路由器R4,同样添加对应VLAN222的IP地址到Wlan1接口上,并创建与VLAN222相同的加密配置,设置无线网卡wlan1的mode=station
[admin@R4] >
/interface wireless security-profiles
add authentication-types=wpa-psk,wpa2-psk eap-methods=”” management-protection=allowed mode=dynamic-keys name=\
vlan222 supplicant-identity=”” wpa-pre-shared-key=yusvlan222 wpa2-pre-shared-key=yusvlan222
[admin@R4] >
/ip address
add address=192.168.2.4/24 interface=wlan1
/interface wireless
set [ find default-name=wlan1 ] disabled=no mode=station security-profile=vlan222
以上配置的也适用于终端笔记本,手机和平板接入,只需要在R1的vlan111和vlan222创建DHCP服务
DHCP服务配置
R1路由器创建DHCP服务,首先创建地址池
/ip pool
add name=vlan111 ranges=192.168.1.10-192.168.1.50
add name=vlan222 ranges=192.168.2.10-192.168.2.50
R1上配置DHCP服务
/ip dhcp-server
add address-pool=vlan111 authoritative=after-2sec-delay disabled=no interface=vlan111 name=server1
add address-pool=vlan222 authoritative=after-2sec-delay disabled=no interface=vlan222 name=server2
/ip dhcp-server network
add address=192.168.1.0/24 dns-server=192.168.1.1 gateway=192.168.1.1 netmask=24
add address=192.168.2.0/24 dns-server=192.168.2.1 gateway=192.168.2.1 netmask=24



